API Licensing 101: Generating Recurring Revenue from Your APIs
APIs (Application Programming Interfaces) have become a vital part of many technology platforms and digital businesses. Companies like Google, Facebook, and Twitter provide APIs that enable other developers to access their technology and data.
What is Software Licensing
Effective software licensing plays a pivotal role in the technology industry, providing users with the necessary legal permissions to utilize a particular product or service. This article delves into the intricate world of software licensing, placing emphasis on critical components like software license agreements, license keys, and diverse licensing models. It also explores the significance of managing software licenses and examines various approaches to software deployment.
NetLicensing: a journey through the highlights of 2023
As we approach the end of another year, it’s almost unbelievable how quickly time has flown. Reflecting on the bustling year that was 2023, we’re overflowing with gratitude for every team member who contributed to NetLicensing’s success.
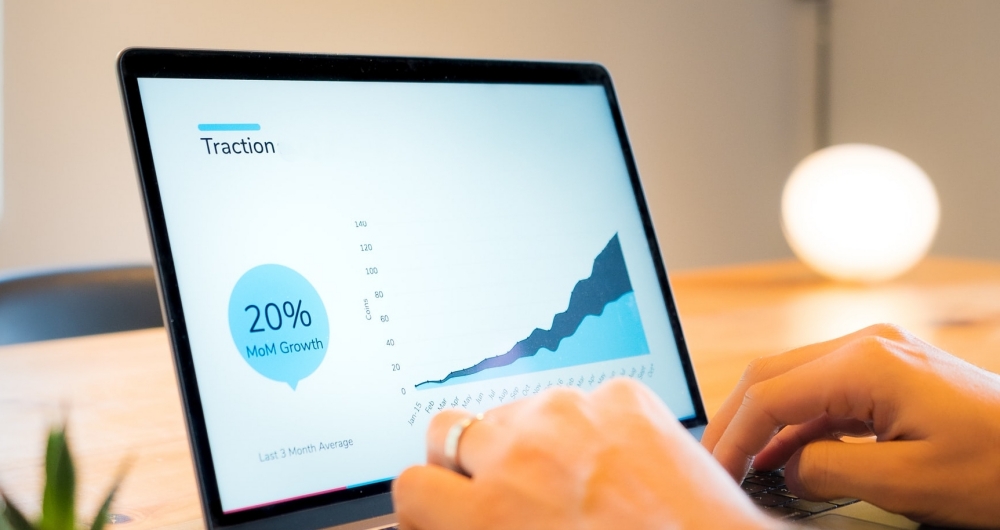
Build, Measure, Learn: The MVP Mantra for Startup Success
Many software developers often fall into the trap of overbuilding their initial product release, driven by the fear that their offering might not be compelling enough for users. However, this fear-driven approach can lead to failure due to excessive resource expenditure. A more effective strategy is to start small with a Minimum Viable Product (MVP), significantly increasing the chances of success. The benefits of an MVP extend beyond cost reduction, positively impacting product quality, efficiency, and customer relations.
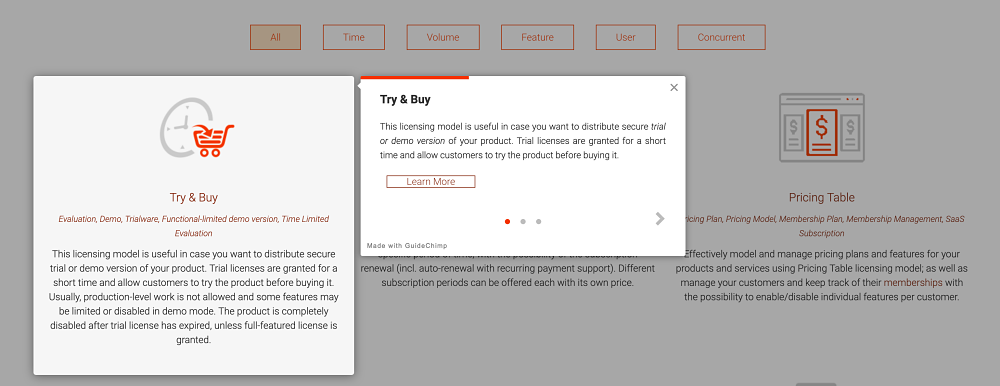
Pricing Table Licensing Model - The Game-Changer
In the dynamic world of software development, choosing the right licensing model can be a critical decision that significantly impacts a product’s success. Among the plethora of options available, NetLicensing’s Pricing Table Licensing Model stands out as a game-changer, offering a myriad of benefits for developers. In this blog post, we will delve into the advantages that this innovative licensing model brings to the table.
Labs64 NetLicensing Cyber Weeks Special - Enjoy a 64% Discount
Embark on a transformative journey with Labs64 NetLicensing as we introduce our Cyber Weeks Offer, an extraordinary 14-day promotion commencing on November 17th and culminating on December 1st, 2023.
Streamlining Cloud Infrastructure Access: Simplifying SSH with ProxyCommand and Wildcards
Building IT infrastructure using cloud services represents a cutting-edge approach for small companies and startups. It eliminates the need to invest in, maintain, and set up physical hardware while providing industry-standard resiliency and security. Typically, this infrastructure involves placing virtual hosts that provide services in a private network and exposing these services over secure protocols like HTTPS through a reverse proxy acting as a gateway accessible from the internet. This setup ensures that the servers hosting the services remain protected from internet-based attacks. However, it can pose challenges for legitimate users who require access to these servers for maintenance. This typically involves a two-step process: first, logging into a gateway server with access to the private network, and then logging into the target server, with SSH being the assumed login method.
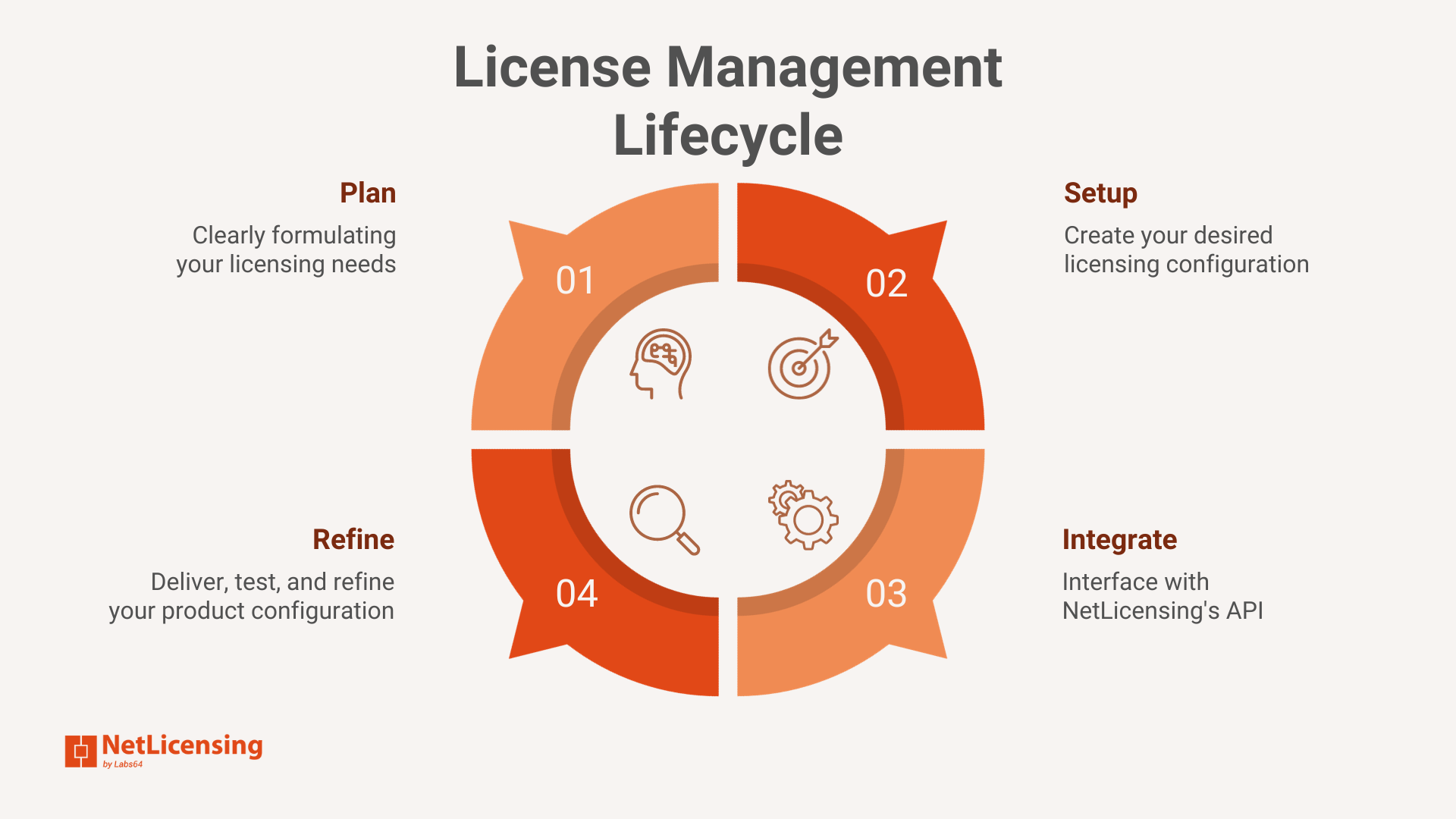
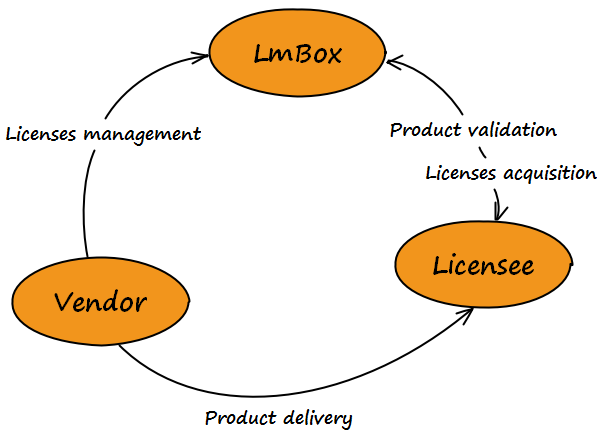
License Management Lifecycle
Setting up NetLicensing License Management services for a vendor’s products involves several steps. Here’s a high-level overview of the process:
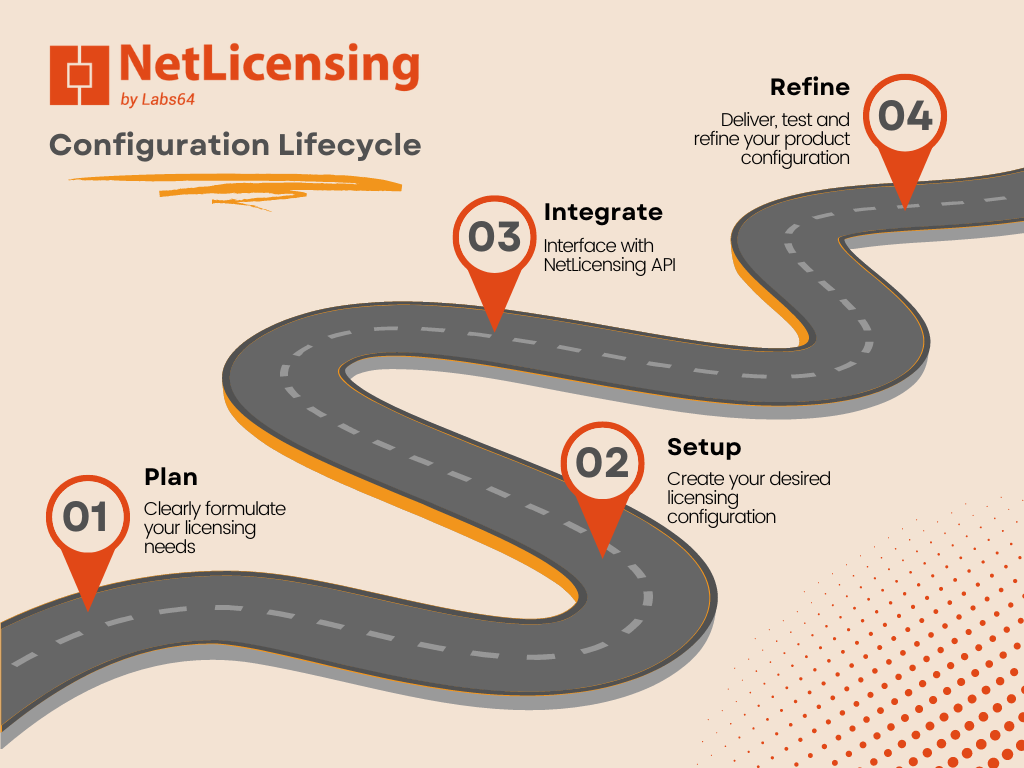
The NetLicensing Configuration Lifecycle: A Comprehensive Guide
The process of configuring and managing licenses is a crucial aspect of any software product or service. NetLicensing, a powerful licensing solution, offers a comprehensive Configuration Lifecycle to help businesses effectively manage their licensing needs. This article will explore the four key stages of the NetLicensing Configuration Lifecycle: Plan, Setup, Integrate, and Refine.
Software Licensing - Comprehensive Guide to Types and Models
Defining Software Licensing
NetLicensing Handbook
Do you know NetLicensing Handbook?! - The NetLicensing Wiki is a comprehensive source of information about our cloud-based licensing management system.
Master Software Licensing with NetLicensing
Software licensing is a crucial aspect of software development, distribution and protection. It ensures that software is used legally, and provides revenue streams for software developers. However, managing software licenses can be complex and time-consuming. This is where NetLicensing comes into play, offering a comprehensive solution to software licensing problems.
Labs64 NetLicensing - Cyber Weeks Offer - 64% OFF
Labs64 NetLicensing is now holding a major 2-weeks promotion that begins on 28th of November and will end on 12th of December 2022.
Labs64 NetLicensing - Orange Weeks Offer - 64% OFF
This year we introduce a new most asked - Labs64 NetLicensing Orange Weeks!
Convert Leads and Grow Your Revenue with Trails
Using License Management Software that gives you the possibility to easily convert trial leads and adopt products will give you a huge advantage with the competition, as your customer base, simultaneously with your revenue, will grow more quickly.
Labs64 NetLicensing - Cyber Weeks Offer - 2020
Also this year we continue most wanted - Labs64 NetLicensing Cyber Weeks!
Onboard users using interactive Product Tours with GuideChimp
Step-by-step interactive guides and feature introduction tours is one of the techniques every marketer should know and adopt nowadays.
How to use NetLicensing with Java and Spring Security
Recently we started a journey through user Authentication-Authorization and entitlements Validation process with the article What is Authentication-Authorization-Validation Framework.
The Worst Nightmares for Account Managers
For many years, whenever a customer decided to change or update its software license, the pain started to come as there were many steps involved in the overall process. It would all start with the discussion of the changes that needed to be made, again issuing original license keys, shifting the files to other software or, in the worse cases, also starting a complete product re-installation - a true horror story for all account managers, support staff and customers’ responsible.
How to evaluate and validate XPath and CSS selectors
There are many scenarios where developers need a valid XPath/CSS selector definition.
Easily update customers’ entitlements
Since a long time, upgrading software licensing has always been seen as a never-ending process which software developer feared. As a customer wants to change their software license plans, many are the steps to follow start from the creation of new license key to moving these licensing & configuration files around or, in the worse cases, also re-install them.
Hacktoberfest @ Labs64
Also this “COVID” year 20x2 won’t be exclusion - #Hacktoberfest has officially started (today) on the October 1st!
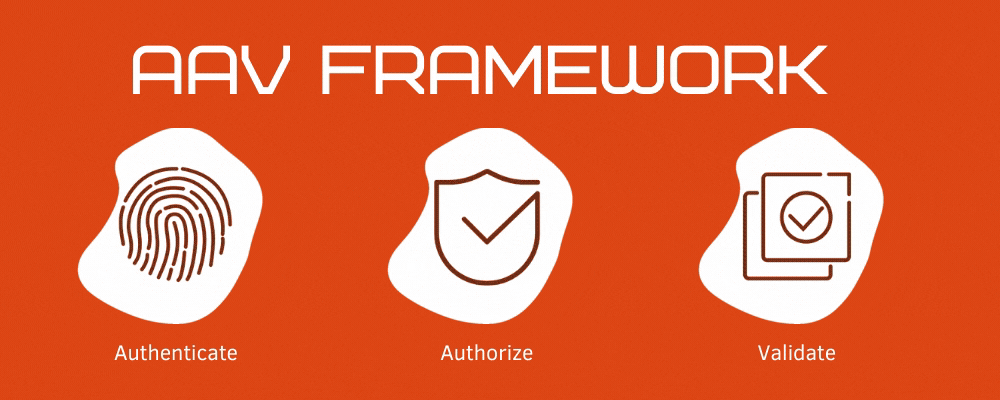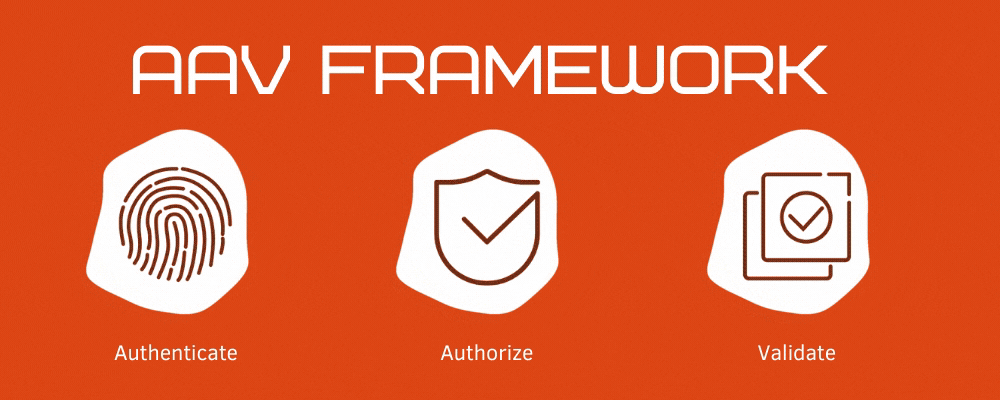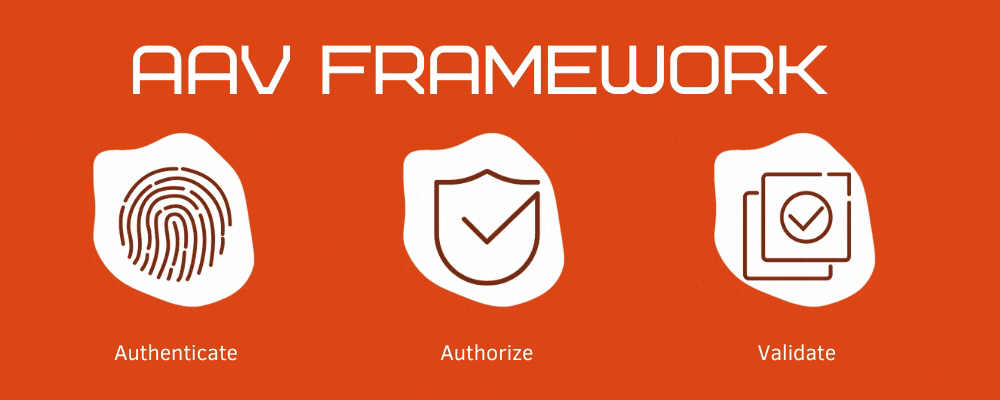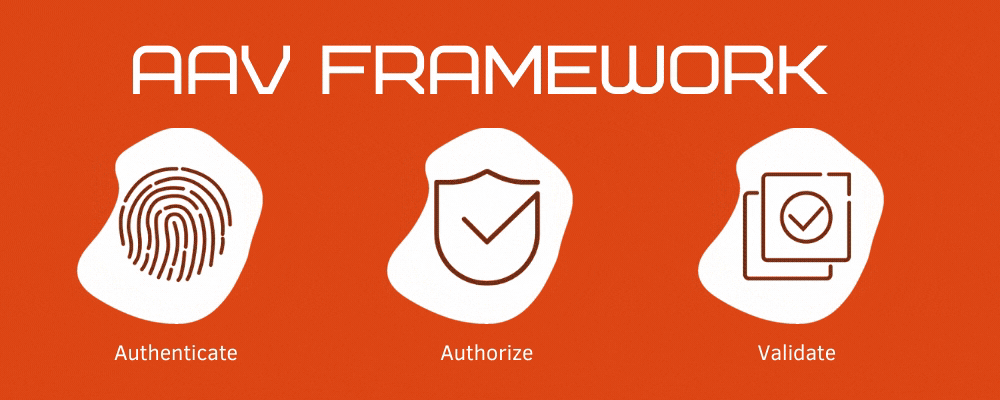
What is Authentication-Authorization-Validation Framework?
Authentication and Authorization are one of the important and integral concepts in software development.
Is Subscription Model Suitable for On-Premise Applications?
As the world’s economy is finally emerging from the current lockdown, the ability to restore growth and achieve sales will be the most challenging task that companies will need to deal with. On-Premise applications, for example, are considered to achieve the best strategy for companies that are not capable of making huge investments for the sake of accelerating the customer buying process.
Publish NuGet packages using GitHub Actions
GitHub Actions: automate, CI, package and push your .NET libraries to NuGet.org
The Impact of a Pricing Table Simplicity
Pricing Tables can be considered as one of the most valuable parts of a website as they are an essential tool for communicating the value and benefits that your company offers to the market. Having a clear pricing table, where customers can instantly understand all the features and the value in your SaaS product will deliver, increases the likelihood to attract paying customers for one of your plans. However, if customers see inconsistencies in your pricing tables and are not able to have a clear understanding of your offering, they will probably consider spending their money somewhere else.
Work Remotely with Flexible Licensing Models
Since Covid-19 pandemic has started, many employees that had to shift to remote working style. However, some studies were able to prove that productivity was decreased by 50% compared to working in the office. The main reason why this issue occurred is that many employees did not have the tools to work with. Thus, SaaS solutions have a strong advantage compare to their on-premise competitors.
Importance of Freemium Pricing Model
Over the past years, a specific pricing model has been trending in the market: Freemium Pricing Model. The Freemium model is a conglomeration of the “Free” and “Premium” model giving the users the possibility to use a product or service free of charge but with a limited number of features. In case they want to get access to a broader number of features, a subscription fee will be required. Each of us, throughout our lives, has been exposed to a “Freemium” model with Apps, TV shows, Cloud services etc. as this model is acquiring more popularity year after year.
Solution to Manage Software Licensing During a Pandemic
As the economic damage created by COVID-19 pandemic keeps raising day-by-day, many of the companies that want to keep their businesses running were forced to adjust their operation in terms of working hours, employees’ layoffs, and strategies to ensure revenue also in a difficult time. Things are tough for companies as there is a strong need to recover from the current downturn and, in such time of uncertainties, maximum flexibility to test different strategies is inevitable.
Increase Sales by Providing Free Trials
The market is currently going through a significant downturn caused by the pandemic. As we have already experienced in the past, the market will surely recover, but new changes will be involved. Working from home will not be an option anymore - thus we will have to deal with a new working model.
Improve Efficiency by Automating Licensing Processes
Nowadays, many independent Software Vendors need to invest a considerable amount of time for managing and keeping track of their customers and their entitlements. Businesses that for the past years have been executing these operations through manual processes can now forget about it and discover a brand-new way to automate the processes with a simple, flexible, and easily integrable platform: Labs64 NetLicensing.
Build Guided Product Tours Using GuideChimp
New customers retention is a big concern for almost every SaaS provider. To engage new customers you need to help them reach “Aha!” moment faster.
Top-5 Programming Languages to Learn in 2020 by Labs64 NetLicensing
Which programming languages will continue to be in demand in 2020 and beyond and how many languages should you know to improve your career chances?
How To: NetLicensing demo account
It was never easier to try NetLicensing in action!
Labs64 NetLicensing - Cyber Weeks Offer - 70% OFF
Also this year we continue most wanted - Labs64 NetLicensing Cyber Weeks! Labs64 NetLicensing is now holding a major 2-weeks promotion that begins on 25th of November and will end on 6th of December 2019.
Labs64 Joker Raffle
Find the Labs64 Joker and get one year Labs64 NetLicensing Basic or Premium Plan for FREE!
NetLicensing 2.5.0 - Indian Summer edition
Today we are happy to announce that we launched a new version of NetLicensing 2.5.0 - Indian Summer edition. We have added a load of new features and improvements to help ISV to enable enterprise-grade license management.
Reliable Product Licensing Systems Benefits
In the past few decades various new businesses and technologies were, and are on the rise. Genetics, new digital products that are basically supercomputers compared to standards just a 10 or so years ago, intelligent cars, new materials - and one that was expected, but is simply coming and taking over way too fast - the Internet.
Market trend: Growing Virtualization of desktops
With increasing use of smartphones, virtualization has taken a different meaning, enabling employees to do a lot more, even on the go. Virtual desktop infrastructure or VDI has gained a wide adoption rate, with 80% organizations already using it in their IT strategy.
NetLicensing - Cyber Week Offer - 70% OFF
Everybody knows that the hottest online sales are found on the Cyber Monday after Thanksgiving. We even go beyond and present Labs64 Cyber Week! Labs64 NetLicensing is now holding a major 1-week promotion that begins on 26th of November and will end on 2nd of December 2018.
Labs64 NetLicensing 2.4.0 is Out!
Just in time for the NetLicensing Cyber Weeks, we are releasing the new version of NetLicensing 2.4.0 - Cyber Edition and we are bringing a bag full of goodies to help ISV enabling enterprise-grade license management.
Labs64 NetLicensing joins new Stripe Partner Program
Labs64 NetLicensing is one of the first to join new Stripe partner program
Get your free CeBIT 2018 tickets
Activate your FREE NetLicensing Vendor Pass for CeBIT 2018
We're updating our Privacy Policy and Terms of Service
Thanks for using NetLicensing and our License Management Services. We constantly strive to ensure our product is exceeding your expectations and adhering to our responsibilities. To that end, we’ve recently updated our Terms of Service and Privacy Policy so it’s clearer and also addresses the new data regulations (including GDPR).
Labs64 NetLicensing 2.3.9 is Out!
Today we launched a whole new reason for software vendors to love NetLicensing: We are excited to announce the release of NetLicensing 2.3.9. We have added a load of new features and improvements to help ISV to enable enterprise-grade license management.
Understanding Software Pricing Models
Licensing is perhaps the biggest issue that many system administrators face and is one which can cause endless issues if it is improperly managed. When it comes to understanding the different pricing models that exist for licensing; a difficult decision becomes almost impossible. In recent years there has been a clear divide between the two main models and we will try to explore those in more detail here. In order to not overcomplicate the discussion; we will refer to them as ‘owned’ (with on-going support) and ‘leased’.
NetLicensing - Cyber Weeks Special - 80% OFF
Everybody knows that the hottest online sales are found on the Cyber Monday after Thanksgiving. We even go beyond and present Labs64 Cyber Weeks! Labs64 NetLicensing is now holding a major 2-week promotion that begins on 20th of November and will end on 4th of December 2017.
Labs64 NetLicensing 2.3.8 - Halloween Edition
Just in time for Halloween, we are releasing the new version of NetLicensing 2.3.8 - Halloween Edition and we are bringing a bag full of goodies.
DNS Issues affecting resolution of .io TLDs
Status update (16:10PM UTC): We are being affected by the intermittent global DNS issues with resolving records on .io domains. All .io domains globally are currently having intermittent issues, causing some issues with our services.
Labs64 NetLicensing - Licensing-as-a-Service
“Licensing” - a word that brings fear to the heart of Software Vendors. Licensing management is complex, time-consuming; and confusing for everyone. The seemingly endless difficulties - operating your own licensing service in 24/7, allocating maintenance resources, a lack of flexibility and the endless hours spent tracking licenses through e-commerce systems not designed for software licensing.
Updates to Labs64 NetLicensing Terms of Service
We updated our Terms of Service
Labs64 NetLicensing 2.3.7 is Out!
At NetLicensing, our promise to you as a software vendor is to make licensing management painless. Following that promise, we are extremely happy to announce the general availability of NetLicensing 2.3.7!
Labs64 NetLicensing 2.3.6 Maintenance Release
This maintenance release targets important compatibility issue:
Happy Holidays & NetLicensing 2.3.5 announcement
Dear Licensing Partner, It’s hard to believe we’re at the end of another fantastic year. We wish you joy and happiness this holiday season and throughout the coming year.
Cyber Monday - Labs64 NetLicensing 2.3.4
On this Cyber Monday, we are happy to announce NetLicensing 2.3.4 availability!
Grace Period License
If you speak to any IT professional about licensing and more specifically about license periods and renewals they will tell you that a major problem for them is tracking the expiration of the numerous licenses they have now. The variety of vendors and software available is now greater than ever. As a result, the number of licenses that IT professionals have to manage has increased and the risk of licenses expiring is now greater than ever.
Labs64 NetLicensing 2.3.3 is Out!
At NetLicensing, our promise to you is to make licensing management painless for software vendors. To that end, we are extremely happy to announce that NetLicensing 2.3.3 is now Generally Available!
Overflow Licenses
Information Technology is constantly evolving and changing. It is estimated that every 18 months computing power doubles. Where IT used to be a company asset, it is now the backbone upon which the majority of businesses conduct their operations. As a result, the number of the devices, their locations, and their uses within a company is constantly changing. All of this technology from servers to clients and mobile devices have one thing in common. They will run software that requires licensing.
Time Zone Licenses
If software licensing is to be competitive then it needs to be both affordable and flexible. This can be increasing difficult for software vendors to achieve as it usually means reducing the price, or enabling the user to do more with the license for the same cost. The issue here is that there is only a certain amount of flexibility and price fluctuation that can be built into a licensing model whilst still remaining profitable. The other major issue with complex and flexible licensing models is that they are harder to sell than traditional licensing models - because they are harder to explain and take up more of both the sellers and customers time, which in turn reduces productivity and profit.
Competitive Upgrade License
All IT Professionals have their own software preferences for email, antivirus, operating system and office suites and they will always tell you why their choice is the right one. Whilst all options have different pros and cons you may from time to time want to change the software used often when there is a change of management and this can be a costly exercise, both in the time taken to migrate to the new software as well the cost of licensing.
Bring Your Own License
It would not be an understatement to say that cloud computing has revolutionized and democratized the technology industry. It has enabled companies to vastly expand their field of operations with almost no upfront cost. Companies comprised of just a few individuals can now easily operate on a truly global scale like never before.
Labs64 NetLicensing 2.3.1 Maintenance Release
We are extremely happy to announce that NetLicensing 2.3.1 is now Generally Available! In this maintenance release, we focused on fixing a few specific and annoying bugs and improvements reported by NetLicensing users.
License Mobility
The concept of license mobility is actually surprisingly easy to understand in essence it means that can reassign your license between devices as and when it is required. For this article, we are going to look at the limitations about options that you have when assigning software licenses in a couple of settings. Specifically, server farms and server repartitioning. We will look at these in more detail shortly, but first we are going to explain the rules of license reassignment, and what is defined as ‘short-term’.
The New Way is the Free Way
If the purpose of a business is to make money, then how does giving your product away for free make sense? – This is the question that has been posed to us since we made our announcement that NetLicensing is going to be made available for free. In fact, the idea of making a basic version of a product freely available, with the option to purchase access to a ‘Premium’ tier has been around for almost a decade.
Understanding Freemium
You may well have heard the term ‘Freemium’ or in the context of mobile or online gaming ‘Free to Play’. It is becoming ever more common as a method of distribution for software and web services and it is likely that you will have taken advantage of ‘freemium’ product even if you have not previously heard the term.
Labs64 NetLicensing 2.3 is Out!
It’s a New Year which means new opportunities and, more importantly, a new version of NetLicensing 2.3 is here.
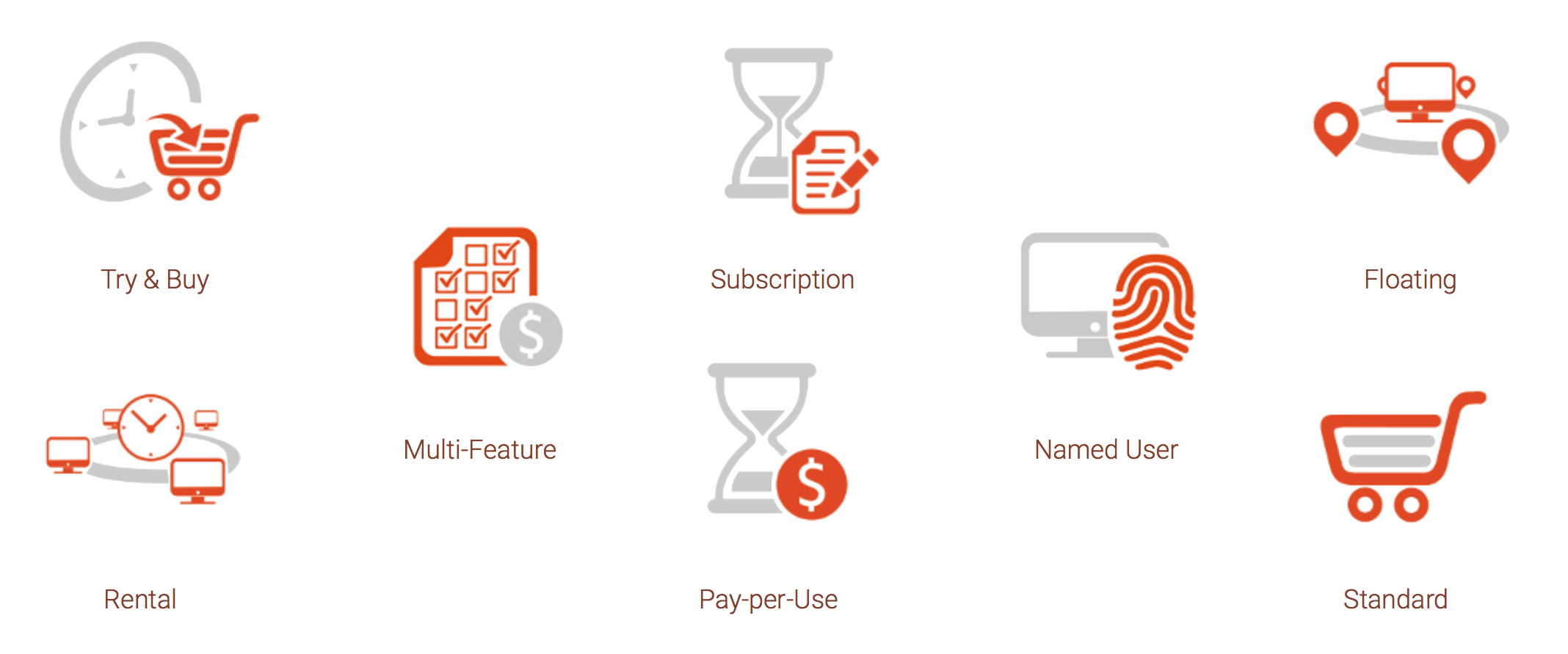
Infographic: How To Select Licensing Model
Labs64 NetLicensing allows you to monetize your products by licensing them to companies or individuals.
Labs64 NetLicensing is going FREE!
Labs64 NetLicensing - Online License Management Service is taking a huge step forward in making it easy for vendors to sign up with their licensing management service.
Internet of Things – Part III
In our last article we briefly looked at the question of how the ‘Internet of Things’ could be set to drastically change the world of licensing. Until now most of us have been familiar with the process of licensing software; and how that model is changing. Significantly, in the past 2 years there has been a noticeable shift away from ‘one-off’ license payments to a ‘subscription’ model. This has made it more affordable for many customers, as it has also seen a shift in the way that the software is distributed. Rather than having annual releases with a two-tiered price model (Upgrade or Buy) with a large amount of software you now pay a fixed monthly fee and receive all updates for as long as you continue to pay the fee.
NetLicensing Can Save Lives
We have always known that NetLicensing is a great product. With the ability to save vendors of all sizes; time, money and effort. Now, it would seem NetLicensing can even save actual lives! We recently received this story in an email from one of our customers, and thought that we would share it with you – maybe NetLicensing could save your (work)life?
Internet of Things – Part II
In our last article we looked at how the internet has become an integral part of our lives, rather than simply being a resource where we find information and a tool that we use to communicate. It is now at the centre of our lives. We are reliant upon it to carry out everyday tasks and for our numerous devices to work properly.
Internet of Things – Part I
It’s a little over thirty years since the first internet domain name was registered, and although a lot has happened to the internet since then. It is still a fairly young technology. It is in this short time that the internet has become a central part of our lives.
Labs64 NetLicensing 2.2 is Out!
Today we’re excited to finally announce the availability of the Labs64 NetLicensing version 2.2.
Licensing in the Cloud
A topic that we have covered on repeated occasions has been the perpetual increase in the number of devices which can access the internet. We have looked at this from a number of perspectives but one that has so far eluded us is the subject of licensing and license activation.
Services Can Add Automatic Image Attribution for Your Website
Stock and custom photos and images can add a nice final touch to your website and blog when making a point. The prevalence of photo sharing services and new digital technologies has made photos more common across the Web, so your content needs to secure stunning images to keep up with the competition.
The benefits of LaaS for software development, deployment and customer service
The movement of infrastructure, processing and networks to the cloud often involves the emulation of software and services that run these cloud-based platforms. Software running in the ether still requires a license, but managing the licensing for virtual machines can become a complex task, especially when a single server or machine may run multiple instances of your software.
Who’s Watching You?
It is undeniable that one of the largest technology stories of 2013 was not a new range of televisions, or a revolutionary smartphone. Although these were both technologies that emerged in this year, the story which saw a UK newspaper destroy computer hard disk drives in the presence of members of the Security Forces and a well-documented man-hunt across half of the world was the revelations released by a former employee of the American National Security Agency that millions of people had had their personal emails and mobile phone records accessed by agencies in both America and Europe.
Is there a decline in personal device usage?
The change in application use is reflective of a broader shift in the way that people interact with the technology around them. Even five years ago, people were not as ‘connected’ as they are now. Increasing broadband connection speeds, wider availability of free Wi-Fi, 3G and 4G mobile networks has meant that we are hardly ever away from the multitude of computers that we now carry with us, wherever we go.
Labs64 NetLicensing 2.1 is Out!
Today we’re excited to finally announce the availability of the Labs64 NetLicensing version 2.1.
The New Way to Pay
The defining aspect of the success of Smartphones over the last five years has been the ability that they have given us to literally do anything we want in practically any place. The phrase ‘there is an app for everything’ has now become common parlance amongst both industry members and consumers alike. We carry in our pockets mini-computers with more power and potential than those which we used in offices just 10 years ago.
Think outside the Box (and your wallet)
You are an inventor, you have a great idea for a new piece of technology but you don’t have the resources to properly explore your ideas and bring them to fruition. You don’t have any great amount of disposable income and there is no one willing to back you. You don’t want to do a half hearted job as you’re worried that if you don’t get it right first time, then you will have lost your chance and your dreams will be over.
‘Specific Use’ Applications
It might seem strange to think that it is now ten years since the largest social network every created was first dreamt up in the dormitory of an American University. It’s uniquely recognisable symbol is everywhere and can be used to access almost everything. It is undeniable that social networking has completely changed the way in which we interact with people as well as how we approach our day to day communications with one another.
Working with Canvas – The new technology of vector animation
Use of HTML5 gives developers new horizons in animation implement for their websites. There is no need to use outdated Flash technology or to overload traffic with large images, you can simply familiarize with a few norms of creation of motion interpretation by canvas redraw.
Application Security: The Essentials – Insufficient Transport Layer Protection
In this, our final article in our series on the essentials of Application Security, we will be looking at Insufficient Transport Layer Protection. This occurs when an application has failed to properly encrypt network traffic, which means that confidentiality and overall integrity has been compromised. ITLP also covers the times when applications network level security is weakened; this can be because of flaws in algorithms, improper use of certificates and use of security certificates which have expired.
Application Security: The Essentials – Failure to Restrict URL Access
It is often the case that applications will contain URL references to its separate pages through the use of protected links and buttons. The content to which you link depends entirely upon the application and its function; however, you should consider every link to be a potential gateway for an attack. Within an application, there is likely to be references to pages which contain confidential or sensitive data and unless you have correctly configured the restrictions; anyone with network access could potentially access private pages.
Apps for Business
In this next article in our ongoing series on the future for application developers, we now turn to applications which are commissioned and made for business. The stereotypical image of a businessman with both his suitcase and email-enabled phone hastiled checking, reading and replying whilst on the go.
Apps in Education
In our recent article, we looked at the question of whether or not an increasingly saturated application market is leading towards an application ‘crash’. There is a strong argument to be made that developing for niche markets is the way forward if companies and developers are to be successful.
Is there an application ‘crash’ looming?
How to keep producing relevant software:
Application Security: The Essentials – Cross Site Request Forgery
We have already looked at how applications which use external references to a browser can be vulnerable to attacks (see Unvalidated Redirects and Forwards). With Cross Site Request Forgery you are dealing specifically with an application which sends HTTP requests to the user’s browser, as a part of its day to day functionality. External URL requests are, as we have previously discussed, a risk because they take the user outside of the boundaries of the application. This means that the level of control which you as a developer have is immediately impeded. However, there are still a number of steps you can take to prevent cross site request forgery.
Labs64 NetLicensing 2.0 is Out
During the past month we’ve been focusing on improving NetLicensing, and today Labs64 team is pleased to announce the availability of NetLicensing version 2.0.
Application Security: The Essentials – Insecure Direct Object References
In the articles which we have already published on the topic of application security, there has been a recurring topic of proper authentication within the application. Applications are built in layers, with different degrees of access being granted to different users; depending upon whether their credentials have been correctly authenticated. Obviously the primary access to the application should be as secure as possible, with timeouts, secure password policies etc. This article will look at the need for secure references within the application.
Future trends in mobile payments
Mobile payment systems are taking root around the globe, reaching major retailers and coffee shops as well as the single-store small and mid-sized boutiques that dot the landscape.
QR Codes are everywhere
Quick Response (QR) Codes are everywhere we go. They are on adverts, in newspapers, on the backs of books and appearing on television screens. They make use of a technology which has been in existence for some time, but that until now has been more common in supermarkets than out on the street.
Application Security: The Essentials – Insecure Cryptographic Storage
In the past few years there has been an exponential increase in the volume of sensitive and confidential data which is being stored by applications and other software. The reason for this change has been a particular drive towards a need for immediacy and ease of use amongst consumers. In short; people now want to do things even faster and with less effort that before. This means that they are entrusting a larger amount of personal data to automated processes within software and applications.
Application Security: The Essentials – Broken Authentication and Session Management
Modern applications frequently handle sensitive data and as such it is common practice for developers to implement varying layers of authentication to access the application. This also means that as a developer you can gather more detailed information about your users i.e. through their email address, which can be used as a marketing tool.
Technology in 2014: Top Emerging Trends
At the start of every new year, there is always a great deal written about what industry experts and writers alike; expect to be the ‘top’ trends for that year. What will be the next big thing? Everyone tries to predict it, and few people often get it exactly right.
Application Security: The Essentials – Cross Site Scripting (XSS)
Cross Site Scripting, or XSS as it is also known, is when the data which is taken by an application and sent to a web browser is done so without proper validation and authentication being carried out first. It leaves the user open to attacking scripts from hackers and hijackers; the effect of this being that they can potentially hijack the user’s session and obtain a vast amount of data.
Application Security: The Essentials – Unvalidated Redirects and Forwards
In this third article on application security, we will be looking at Unvalidated Redirects and Forwards, an uncommon flaw but one which can have a damaging effect on your company’s reputation as it targets your customers rather than you directly.
Application Security: The Essentials – Proper Security Configuration
Welcome to our second article on application security, a guide to the essentials. In this series we are conducting an overview of the major security risks and concerns which present themselves to companies who are looking to move into the highly profitable area of application development.
How to Safely Implement BYOD
The age of the Internet is coming to your employees’ pockets as the Bring Your Own Device (BYOD) trend continues to sweep across industries all over the world. Employees already use their smartphones to check email, send out company updates and schedule meetings. Allowing employees to conduct these and other company business on their smartphones, tablets, and laptops can be dangerous when left unchecked, but proper BYOD policies and software can keep your mobile operations safe.
Application Security: The Essentials – Injection
In this next series of articles we will be looking in some detail at some of the major risks which present themselves to creators and users of applications. We will not be targeting developers themselves, but those of you who either run a business or are looking to get started in the world of application development this is good place to start. You will often be dealing with large amounts of highly sensitive data and security is there absolute paramount to your operation.
Trends in Application Development – Stay Ahead
If your company is to stay ahead in the highly competitive market of application development it is imperative that you stay on top of all of the latest trends, as the consumer will likely already be several steps ahead of you. You should also bear in mind that every single one of your competitors will be pouring as much, if not more, time and money researching the latest trends and seeking out new ways to be innovative.
Paywall – making users pay for what they see online
A question which has often presented itself to the producers of News and Media content for the internet is how to make their work pay in an environment where the expectation is that all content can be easily accessed and most of the time for free. Consumers are naturally drawn to the content which is readily available and free. If they can find a free alternative, then they will stop paying for a service. That is, unless the quality of the paid service is of a good enough value, and a high enough quality that the consumer will be prepared to pay.
The Ins and Outs of Outsourcing
If you run a medium to large sized business you will likely have considered outsourcing at some step along the way to building your successful company. Even if you have only recently started out as a small business with just a handful of employees you may well have built outsourcing into your five or ten year plan for the company’s infrastructure.
Software Licensing Metrics – Machine Compute Capacity
Welcome to this final article on software licensing metrics, we hope that you have found it both interesting and informative. In this last article we will be looking at Machine Compute Capacity as a license metric.
Thinking big about small business data backups
One hazard of operating a small business is thinking that your data backup plans have to be small too. Data backups are essential to maintaining your business, especially as databases grow and press the limits of your hardware.
Software Licensing Metrics – Physical Machine
In this series of articles on software licensing metrics we have so far covered a range of different metric types which measure the process or task carried out by the software in a variety of ways. In these two final articles in the series, we will be looking at Physical Machine and Machine Compute Capacity as metrics.
Software Licensing Metrics – Concurrent User
In our last article on software licensing metrics we discussed ‘Named User’ as a unit of measurement. In this article we will be looking at ‘Concurrent Users’ which is easily confused with Named User as they both rely on measuring the usage level according to the number of users. The crucial difference, which we will elaborate on more in a moment, is that where the Named User uses either the number of logins, Users with access or the actual CPU usage by each user – Concurrent users relies on the number of simultaneous uses. A seemingly minor, but still important distinction.
Software Licensing Metrics – Performance
In our most recent article on software licensing metrics, we looked at the Managed Capacity metric which enables you to distribute different types of software to a wide range of customers of different sizes and charge them accordingly. In this article we will be looking at the Performance metric, which is a little harder to define, but is still worth considering as it comes under the same banner as Managed Capacity metric – namely a metric which does not measure the individual aspects of the software’s use but rather the overall service which it provides to the customer.
Lifecycle of a Website - from Development to Maintenance
The lifecycle of a website consists of various phases. It starts from information gathering, design and development of the website and finally the maintenance phase makes it a constant attention seeking process.
Software Licensing Metrics – Managed Capacity
The common theme which has run through all of our previous articles on software licensing metrics is how to find the best metric for your product and customer base. Acknowledging that every use of the software will be different and hopefully providing you with some information which will help you to make the right decision. The three types of metric which we have covered so far have been reliant upon a pre-determined installation or permissive use of the software by a user. This article is about a metric which fits into a rather different category, it is a metric which does not measure individual uses or installations of the software but rather measures the size of the overall task which the software is used to perform.
The Consumerization of IT – Introducing Bring Your Own Device
The modern world is a minefield of potential lawsuits, with every turn we are faced with more and more pitfalls and traps presented by the ever increasing availability of technology. If you are a business owner you will be all too aware of the ongoing ‘Consumerisation of IT’: namely the increased use within the business environment of personal devices. Whether this be tablets, mobile phones or in an increasingly rare case – laptops.
Correct Use of Stock Images on your Website and Publications
The effective use of images and photography on your website and blog can have a massive impact upon the message which you convey to your customers. A phrase which is well known and perhaps now a little too often used – a picture speaks a thousand words – is actually truer now than ever before. The advent of ever smaller technology and a greater degree of reading ‘on the go’ it has become absolutely paramount to make you website content as eye-catching as possible. If you have strong title and header image people are more likely to bookmark any blog posts of yours which they are linked to by friends and colleagues, than those which are pure text.
Software Licensing Metrics – Named User / Role
Hello and welcome to this next article in our ongoing series on Software Licensing Metrics. In this article we will be looking at what is considered by some companies to be the most cost-effective of all metrics – ‘Named User’. It is, in principle a very straightforward metric to understand. If your customers business operates using a Group Policy where each user is assigned a unique login then a Named User can be an easy to implement means of managing their license costs.
SaaS vs. Traditional Software Licensing Model
Software as a Service has been instrumental in harnessing benefits of productivity of man and organization in working environment by delivering a diverse range of remotely maintained applications over the Internet. Unlike Traditional Software Licensing Model, SaaS strives to resolve the inflexibility of software that arises during maintenance and evolution. Software as a Service model is user friendly and incurs comparatively lower cost.
Software Licensing Metrics – Instance / Installation
Hello and welcome to this next article on Licensing Metrics, we’ve already covered some more general points about Licensing Metrics in two previous articles which it would be worth reading if you are new to the topic of Licensing Metrics. In this next stage of articles on Licensing Metrics we will be looking more specifically at different types of metrics, usually one per article, the different pros and cons of each and how they work in real-world use. If you are familiar with our previous series on Software Licensing Types then you will know how we structure these articles and what you can expect from them.
Software Licensing Metrics – Know Your Rights
Hello and welcome to our third article on Software Licensing Metrics. You’ll need to have read the first two articles in order if you’re going to get the most out of this one which will cover the importance of the definition of rights in an agreement over license metrics. We will look at the common problems which vendors encounter; the common disagreements which often occur, some possible methods which you can use to avoid those, management methods for when disagreements do happen and the best course of action which you can take to avoid losing business.
Software Licensing Metrics – The Value of Simplicity
At the heart of an effective software metric system is its inherent simplicity and the ease of explanation granted to the vendor. The key to selling a product well is the first impression it makes on the customer. Although every salesperson will always say when they are talking to a potential customer they want to keep as far away from discussion of the price as possible; it is often the deciding factor in the decision by a business or individual about whether or not to purchase a piece of software or a service.
Software Licensing Metrics – What are they?
As a company who distributes software to both domestic and business customers, it is important to ensure that you are charging the right amount for the products which you are distributing. In order to give your customers the best value possible, you need to make sure that your price is competitive and that it reflects the usage of the software.
Software Licensing Models – OEM, Time Limited and Upgrade Licenses
In this, our last article in our series on Software Licensing types, we will be looking at three final licensing types: OEM, Time Limited and Upgrade. The reason that these have been left to our last post that that they do not easily ‘fit’ within a certain group of license types and their uses are arguably esoteric. They have a limited field of use and are only useful to a small selection of end-users.
Software Licensing Models – Cross License and Duplicate grouping
This is now our seventh article, in our ongoing series on different software licensing models, their benefits and uses. We are now nearing the end of this particular series and as a result, the final couple of articles will see us cover those license models which we haven’t found space for previously. Rather than focusing on a specific type of licensing model in each article we will be covering a variety of types which link back to those which have already been discussed.
Software Licensing Models – Feature and Exclusive Software Licenses
Hello and welcome to this next article in our ongoing series on Software Licensing Types. If you are new to this series it would be worthwhile reading the previous articles which you can find on our blog. The first post has more detail about what it is that these articles are doing and you will also find our discussion in this article more useful if you have read those which come before it.
Software Licensing Models – Usage and Performance Licenses
It is likely that when they are investigating a new piece of software in which they are considering investing, your customers will want to be sure that they get the absolute best value for their money. In your position as a vendor, it is worthwhile building strong relationships with your customers by always helping them to get the best deal possible. This will save them money in the short term and help build stronger relationships in the long term.
Software Licensing Models – Personal, Node-locked
Hello and welcome to this next article in our ongoing series on software licensing types. It would be worthwhile reading the first post in this series before any others – but after that it doesn’t really matter in which order you read them! This article does follow on from the types of licenses discussed in the previous one, namely licenses which are likely to be used by your business customers.
Software Licensing Models – Floating and Group
In this third article of our ongoing series about Software Licensing Types (see here for the first and second articles) we will be looking at Floating (concurrent) network licenses, Floating (concurrent) host list licenses and Group Licenses. These are best applied in medium to large businesses; however they may also hold some benefits for smaller businesses. This is particularly true where we are dealing with a piece of software that will be used by a large number of people.
Software Licensing Models – Beta and Development
In this second article in our series on software licensing models, we’ll be looking at two more types of software license: Beta and Development. If you haven’t already done so, then we’d suggest you read the first article in the series as it has more detail about what software licenses are, how they are relevant to you and your business and it also covers the four ‘main’ types of software licenses which are available to you.
Software Licensing Models – Types, Sizes and Uses
If you’ve ever purchased a piece of software you’ll have been given a software license key by the manufacturer. This would either have come in the case or have been sent out in the software documentation. The Software License Key is the unique string of numbers and letters which identifies the software as legitimate and which enables you to use all of the features it has to offer.
LmBox 1.0.0-Final released
The LmBox team is pleased to announce the availability of LmBox version 1.0.0-Final.
LmBox 1.0.0-RC4 is available
The LmBox team is pleased to announce the release of LmBox version 1.0.0-RC4.
SVN / Git : side-by-side command reference
In our projects we use both SVN and Git and know how difficult sometimes it can be to mentally switch from one version control to another. As an aid, we created for you this hands-on SVN / Git side-by-side command reference:
LmBox 1.0.0-RC3 is available
The LmBox team is pleased to announce the release of LmBox version 1.0.0-RC3.
Operating as a Service: Different Choices from SaaS to LaaS
The cloud has become an integral part of our daily lives. For business cases, we typically refer to the connection and all of our data interactions as taking place in the cloud. This has led to a rise of many new terms starting with the ever-present Software as a Service (SaaS).
LmBox 1.0.0-RC2 is available
The LmBox team is pleased to announce the release of LmBox version 1.0.0-RC2.
LmBox 1.0.0-RC1 is available
We pleased to announce the availability of the first release candidate of our Innovative License Management Solution LmBox.
How to set environment variables in windows shortcut?
I faced this problem when installed Inkscape (GNU GPL licensed SVG editor) with multiple language packs. Once I started the Inkscape for the first time, I got the UI in German language. Not nice, I wanted it in English. So, I started to look where can I switch the language, and surprisingly I didn’t find this option. Also there appeared to be no command-line switch for it. A brief search on the Web revealed that the Inkscape shows its UI in default system locale (which is German in my case), unless locale is overridden by the LANG environment variable. Tested from the command line – worked like a charm. So far so good, but I don’t like to start Inkscape from the command line each time.
DNS provider comparison
In general, there are many providers where you can get DNS hosting services for free. This, however, is not always the best choice as you only get a basic service.
Recommended Agile Books
Let us begin with some good Agile Book recommendations! Here is a short list of titles that I really found helpful…
The Agile Principles
- Our highest priority is to satisfy the customer through early and continuous delivery of valuable software.